Hybrid scan
Efficient
Pay per bug
Wiseep has a hybrid perspective that combines different ways and techniques to find out vulnerabilities. We perform security tests for a reasonable scanning fee, then you only have to pay if a vulnerability exists.
50+
60+
2560+
1670+
Identifies all weak points
Accepting scopes as an input, processing them,
giving back vulnerabilities as an output.
Targets in your scope are only inputs we accept.
Scopes as an input
Definition
We define most suitable scan engine for your assets.
Scan
Our scan engine perform all necessary tests.
Vulnerabilities in your systems will be an output for you.
Bugs as an output
Process to get rid of bugs
It is possible to get rid of all exploitable vulnerabilities in your systems with 5 simple steps.

It all begins with getting a suitable scanning service for your systems. We will take a complete picture of your scope assets. Your systems will be subjected to thousands of security checks such as technical, well-known, network level, and business logic vulnerabilities will be checked.

After choosing a scan service for your systems, decide a suitable pricing plan considering your budget. We provide different types of pricing plans. Choosing a pricing plan is important because it will affect your scanning fee and payments for vulnerabilities after scanning.

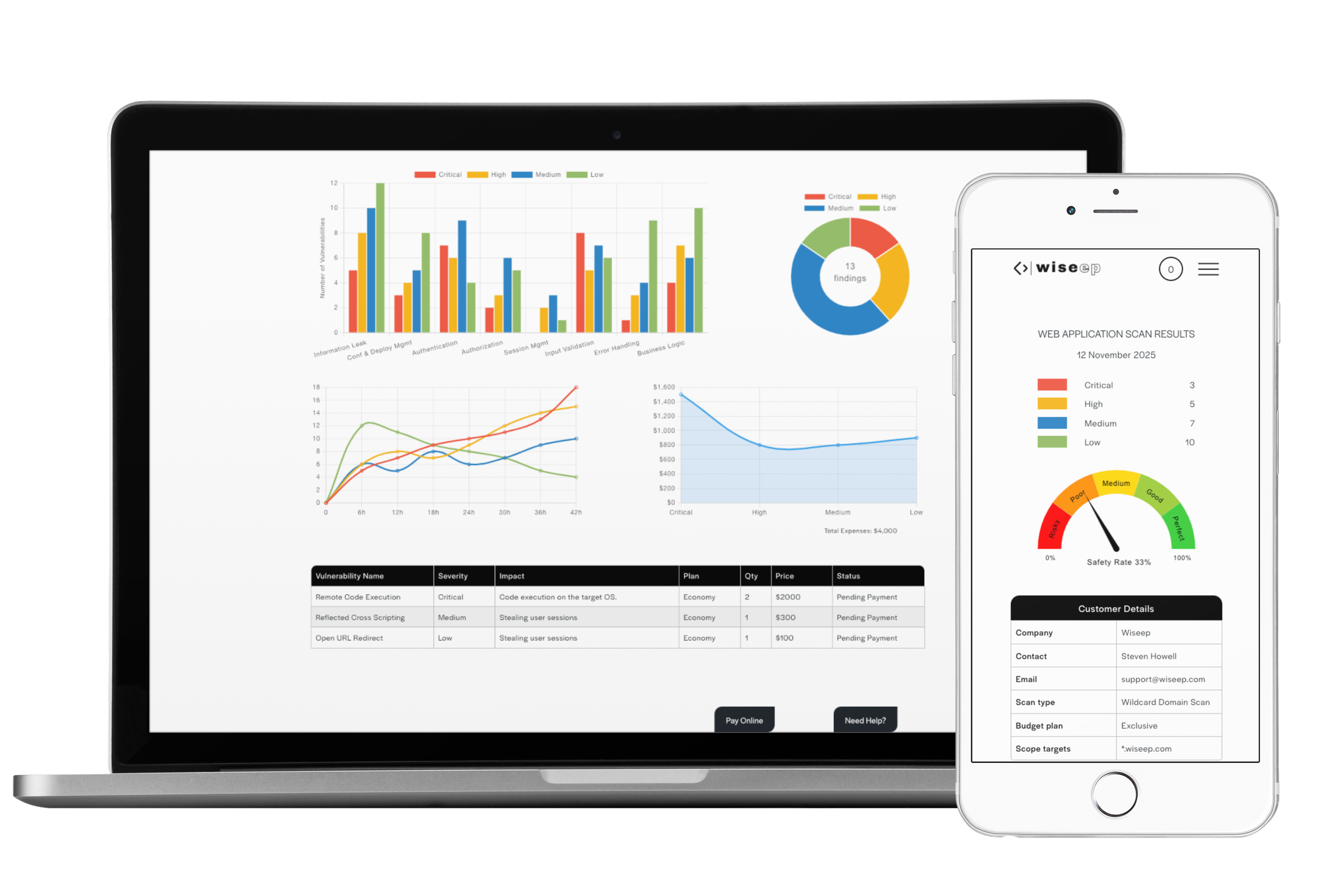
After the scan progress has been done, we will notify you of the security vulnerabilities detected in the tests, including their severity and impact. You can bring any of these security vulnerabilities to the payment stage to learn details and fix.

It's time to pay for the vulnerabilities you care about. By making these payments with the "Budget Plan" used when scanning, you will have the POC and all the details of these vulnerabilities. By paying only if you have a vulnerability, you will get rid of security concerns at a low cost.

You now have all the details of all the security vulnerabilities your systems have. It is time to take action and fix the relevant vulnerabilities by sharing them with your relevant employees. You can request a free retest after finishing all to see whether the vulnerability has been closed or not.
Dealing with big scopes?
Wildcard domains such as *.wiseep.com challenge you?
If you have wildcard domains such as *.wiseep.com and don’t know how to deal with, time to meet with Wiseep. We will do all for you.
Reconnaissance
Finding subdomains, passive checks, data leaks, OSINT controls and more
Scanning
Technical and business logic issue check, network level bugs, CVEs and more
Preparation
Check ports and services, creating URLs, fuzzing, crawling and more
Reporting +
Learn vulnerabilities with severities, pay bugs you care about, just fix bugs
POINT OF VIEW
Makes Wiseep different
See what sets our solution apart.
Wiseep allows customers to learn and fix their vulnerabilities in an easy and affordable way.
Explore Abilities of Wiseep >
Finding bugs before hackers
Budget friendly approach
Ability to scan any scope
Multiple wildcard domain scan
Quick and efficient solution
Pay only for bugs you care about
Assists firms of all sizes
We have different scanning services suitable for companies of all sizes. Whether you are a startup, small-sized enterprise, medium-sized enterprise or larger corporate, wiseep has the capacity to scan for all types of scopes of companies of all sizes. You can take a look at the scanning services we recommend below to meet your needs.

Startups generally need to scan their promotional website and a web portal accessed through a user account. Have a look what does wiseep suggest?
We suggest Single Domain Scan and Credential Scan for Startups, but this may still vary from company to company.

Small sized enterprises usually need to scan their small amount of subdomains and IP address. Have a look what does wiseep provide for your startup?
We suggest Single Domain Scan and Infrastructure Scan for them, but this may still vary from company to company.

Medium sized enterprises usually have one wildcard domain, mobile apps, some network subnets. Have a look what does Wiseep suggest for those?
We suggest Wildcard Domain Scan, Mobile App Scan and Infrastructure Scan for them, but this may still vary.

More assets such as more than one wildard domain, big subnets, mobile apps, code review, desktop apps. Have a look Wiseep's solutions for those?
Large corporations has different types of assets to scan, therefore we suggest to have a look all our scan options.
Latest statistics?
Wiseep has made incredible contributions and statistics to build a secure internet by helping customers to fix the security vulnerabilities identified. Wiseep's findings have been awarded by dozens of Fortune Global 500 companies and many companies of different sizes and sectors.
3.7K+ Scans done
350+ Customer brands tested
240K+ URLs tested
2.6K+ Issues discovered
500K+ USD paid for bugs
460+ Projects completed
Ready for a free start?
Let us uncover vulnerabilities your systems have.
Learn vulnerabilities on your systems for free with our quick scan service for following scans.
-
Have you got a wildcard scope such as *.wiseep.com and need to know your vulnerabilities? Let’s try this free trial scan. You will have this scan service for free with quick scan profile that means scan will not be a fully detailed check. If you have any vulnerabilities you will need to pay for only them by choosing a plan.
TRY FREE >
-
Have you got only subdomains such as admin.wiseep.com and need to know your vulnerabilities? Let’s try this free trial scan. You will have this scan service for free with quick scan profile that means scan will not be a fully detailed check. if you have any vulnerabilities you will need to pay for only them by choosing a plan.
TRY FREE >
Technical vulnerabilities
Business logic Vulnerabilities
Network level issues
Well-known vulnerabilities
Sensitive data leak
Latest CVE issues
Who rewarded us?
Wiseep helps institutions stay safe with great results.
Wiseep is constantly tested in the bounty hunting programs of world-famous companies after regular developments outside of its own customers. Hundreds of companies, some of which are given below, have rewarded their wiseep outputs.
Frequently asked questions
-
Wiseep is an online security service that performs security scans for all type of digital assets such as wildcard domains, single domains, scans with credentials, mobile apps, desktop apps or infrastructure scopes. Apart from a small service fee, it charges according to the risk status of the security vulnerabilities identified. It is a solution that the customer can pay for if they have a security vulnerability.
-
Wiseep performs the security checks that are fully compatible with the relevant scope on the scope it receives from the end user, with the most ideal payload amount, using a hybrid scanning perspective developed with both an automated and partially manual perspective. Scope is passed through all penetration testing steps from A to Z. Outputs are only reported to the user with their risk and POC if they are likely to pose a risk.
-
Users can start the service with a low scan fee and only pay if there is a security vulnerability, so they can be sure of the security of their systems with this small scan fee. If there are security vulnerabilities that will jeopardize the security status of the institution after the scan, they can use their budget in the most efficient way by paying only for these vulnerabilities.
-
The pricing varies depending on the scope type and the payment plan chosen by the customer. There are prices to be paid according to the severity of the security vulnerabilities in the payment plan, the end user can purchase the scanning service by choosing the payment plan that best suits their budget. There is an inverse proportion between the severity of the security vulnerabilities and the scan fee. For example, if a lower scan fee is desired, a payment plan with a higher payment per severity should be selected.
-
The system works with the logic of taking input and giving output. It goes through scan engines that recognize inputs and perform relevant security scans, and is exposed to all kinds of stages, such as information gathering, fuzzing, port scanning, service scanning, URL creation, uniq stages, and finally discovering of vulnerabilities. For the identifying of vulnerabilities and the same tests from other processes, checks are performed by more than one scanners and modules.
If there are more topics you are curious about, you can visit, "FAQs" or "Contact us".